SHA-512/256 Generator
Created on 28 September, 2025 • Generator tools • 126 views • 3 minutes read
Learn about SHA-512/256: a secure, efficient hash algorithm. Uses, advantages, and generator tools.
SHA-512/256 Generator — High Security with Optimal Efficiency
Introduction
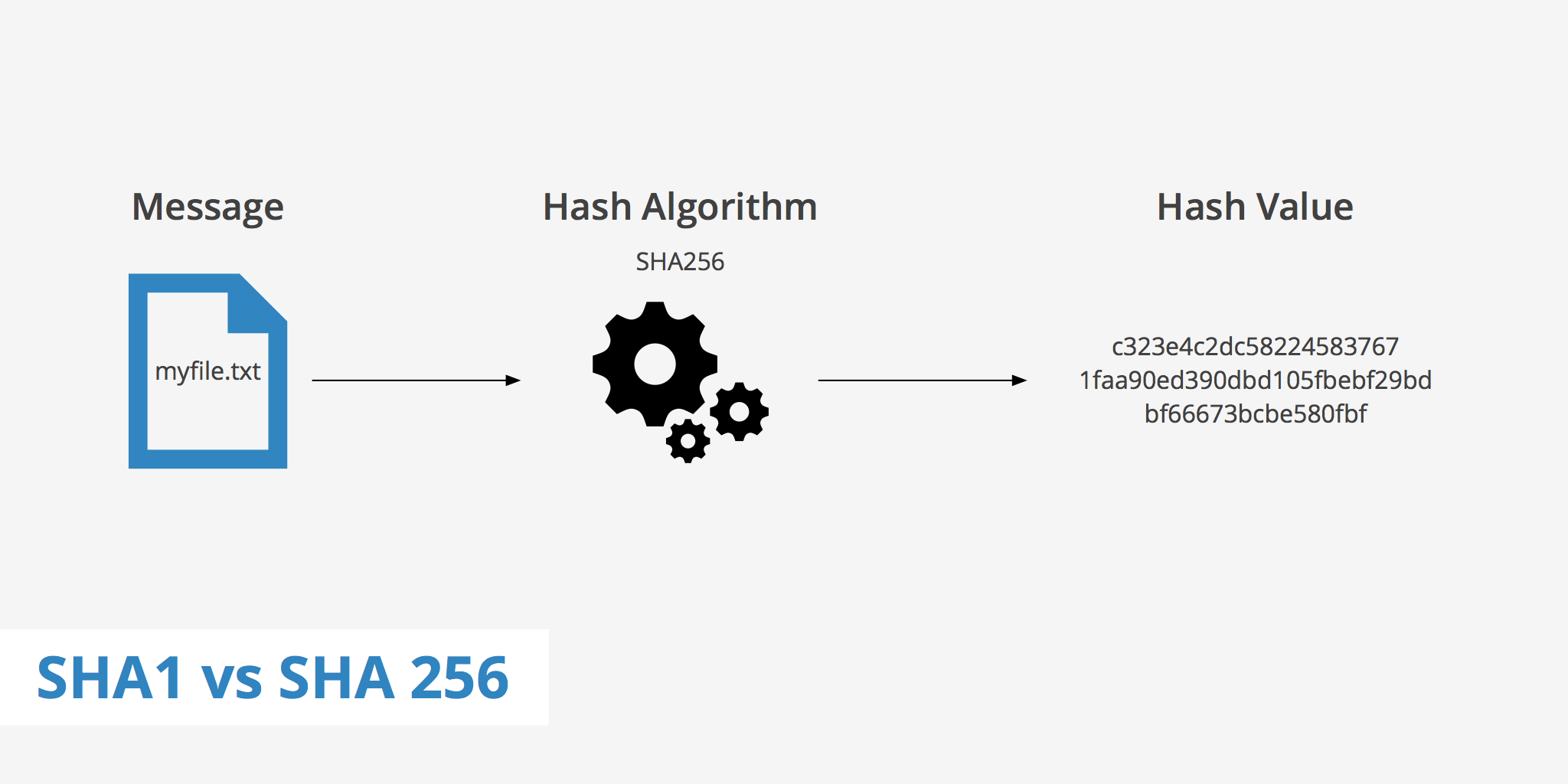
In modern cybersecurity, hashing algorithms are crucial for protecting data integrity, verifying files, and securing sensitive information. Among the advanced algorithms, SHA-512/256 stands out as a high-security, efficient hashing method.
The SHA-512/256 Generator from ProfileLinks.xyz provides users with a fast and reliable way to convert any text, password, or file into a secure 256-bit hash while retaining the internal robustness of SHA-512. This makes it ideal for applications that require strong cryptography with compact output.
What Is SHA-512/256?
SHA-512/256 is a member of the SHA-2 family of cryptographic hash functions developed by the National Security Agency (NSA). It uses the internal structure of SHA-512, but the final output is truncated to 256 bits (32 bytes) instead of 512 bits.
This approach offers:
- The high internal security of SHA-512
- A smaller hash output for better storage and efficiency
- Compatibility with modern cryptographic standards
Example:
- Input: ProfileLinks.xyz
- SHA-512/256 Hash: a2f94c6d2e8f4c7c12d8f915ffeb7c4a9d96326f020b84b26b1f9d2c1c1ab1d3
How SHA-512/256 Works
SHA-512/256 follows the same procedure as SHA-512 with a few modifications for output truncation:
- Message Preprocessing Input data is converted into binary and padded to a multiple of 1024 bits.
- Message Scheduling The padded message is divided into 1024-bit blocks, then expanded into 80 64-bit words.
- Compression Function Each block is processed through 80 rounds using logical functions, bit rotations, and constant values.
- Digest Truncation The final 512-bit SHA-512 hash is truncated to 256 bits, resulting in the SHA-512/256 hash output.
This ensures the strength of SHA-512 internally while producing a concise 256-bit hash for practical use.
Why Use SHA-512/256?
SHA-512/256 is designed to balance security and efficiency. Here’s why it’s widely used:
- 🔒 High Security: Shares SHA-512’s internal structure, resistant to known collision and preimage attacks.
- ⚡ Optimized Performance: Faster than SHA-512 but stronger than SHA-256 in some 64-bit systems.
- 💾 Compact Output: 256-bit hash is ideal for storage, database entries, and network transmission.
- 🧩 Versatile: Used in password hashing, file verification, digital signatures, and cryptographic protocols.
Applications of SHA-512/256
1. File Integrity Verification
SHA-512/256 ensures downloaded files are authentic and haven’t been tampered with by comparing hash values before and after transfer.
2. Password Protection
When combined with salts and key-stretching algorithms, SHA-512/256 provides strong password security, protecting against brute-force and dictionary attacks.
3. Digital Signatures
Used in signing applications where data integrity and verification are critical, such as in SSL/TLS certificates and secure messaging.
4. Blockchain
Some blockchain systems implement SHA-512/256 to verify transactions, reduce hash size, and maintain security in ledger operations.
5. Cryptographic Protocols
SHA-512/256 is integrated into authentication and encryption protocols for secure communications and token generation.
How to Use SHA-512/256 Generator
Using the SHA-512/256 Generator on ProfileLinks.xyz is simple:
- Enter the text, password, or data you want to hash.
- Click “Generate SHA-512/256 Hash.”
- Receive the unique 256-bit hash instantly.
- Copy the hash for verification, storage, or security purposes.
The generator works entirely in-browser, ensuring privacy and no data logging.
Advantages of SHA-512/256
- ✅ Strong Security: Benefits from SHA-512’s internal complexity.
- ✅ Efficient Output: 256-bit hash reduces storage and bandwidth needs.
- ✅ Collision Resistant: Nearly impossible for two inputs to produce the same output.
- ✅ Versatile Applications: Ideal for passwords, files, blockchain, and SSL certificates.
- ✅ High Performance: Optimized for modern 64-bit processors.
SHA-512/256 vs Other SHA Algorithms
AlgorithmBit OutputSecurity LevelPerformanceUse CaseSHA-1160 bitsWeakFastLegacy systemsSHA-256256 bitsStrongEfficientGeneral useSHA-384384 bitsVery StrongModerateEnterprise securitySHA-512512 bitsExtremely StrongSlowerMaximum securitySHA-512/256256 bitsVery StrongFast on 64-bitEfficient secure hashing
SHA-512/256 offers the best of both worlds: SHA-512’s internal security with a compact 256-bit output, making it suitable for modern applications where both speed and safety matter.
Best Practices for SHA-512/256
- 🔐 Use Salting: Enhance password security by combining SHA-512/256 with unique salts.
- 🧱 Combine with HMAC: Ensure secure message authentication.
- ⚙️ Transmit Over HTTPS: Always use encrypted channels to prevent interception.
- 🔄 Regular Updates: Stay current with cryptography standards and best practices.
Educational and Practical Benefits
The SHA-512/256 Generator is also a learning tool for developers and students:
- Observe hash variations with different inputs.
- Understand the avalanche effect in cryptographic hashing.
- Compare SHA-256, SHA-512, and SHA-512/256 outputs.
- Learn about real-world applications in blockchain, SSL, and digital security.
Why Choose ProfileLinks.xyz SHA-512/256 Generator
ProfileLinks.xyz provides a fast, free, and secure online SHA-512/256 generator:
- Works directly in the browser with no installations.
- Guarantees instant hash generation.
- Ensures privacy and security — no data is stored.
- Supports learning, testing, and practical cryptographic needs.
Conclusion
The SHA-512/256 Generator is an ideal tool for anyone who needs fast, secure, and compact hashing. Combining the strength of SHA-512 with a 256-bit output, it delivers high-level protection with efficiency suitable for modern computing environments.
Whether for file verification, password security, blockchain, or cryptographic applications, SHA-512/256 provides a perfect balance between performance and security.
Use the ProfileLinks.xyz SHA-512/256 Generator today to generate reliable, tamper-proof hashes and strengthen your digital security infrastructure.
Popular posts
-
Random number generatorGenerator tools • 171 views
-
Emojis removerText tools • 168 views
-
Lorem Ipsum generatorGenerator tools • 165 views
-
Reverse lettersText tools • 159 views
-
Old English text generatorText tools • 158 views