SHA-512/224 generator
Created on 28 September, 2025 • Generator tools • 126 views • 4 minutes read
Learn what SHA-512/224 is, how it works, its advantages, and how to generate secure hashes in 2025.
SHA-512/224 Generator — Balanced Security and Performance
Introduction
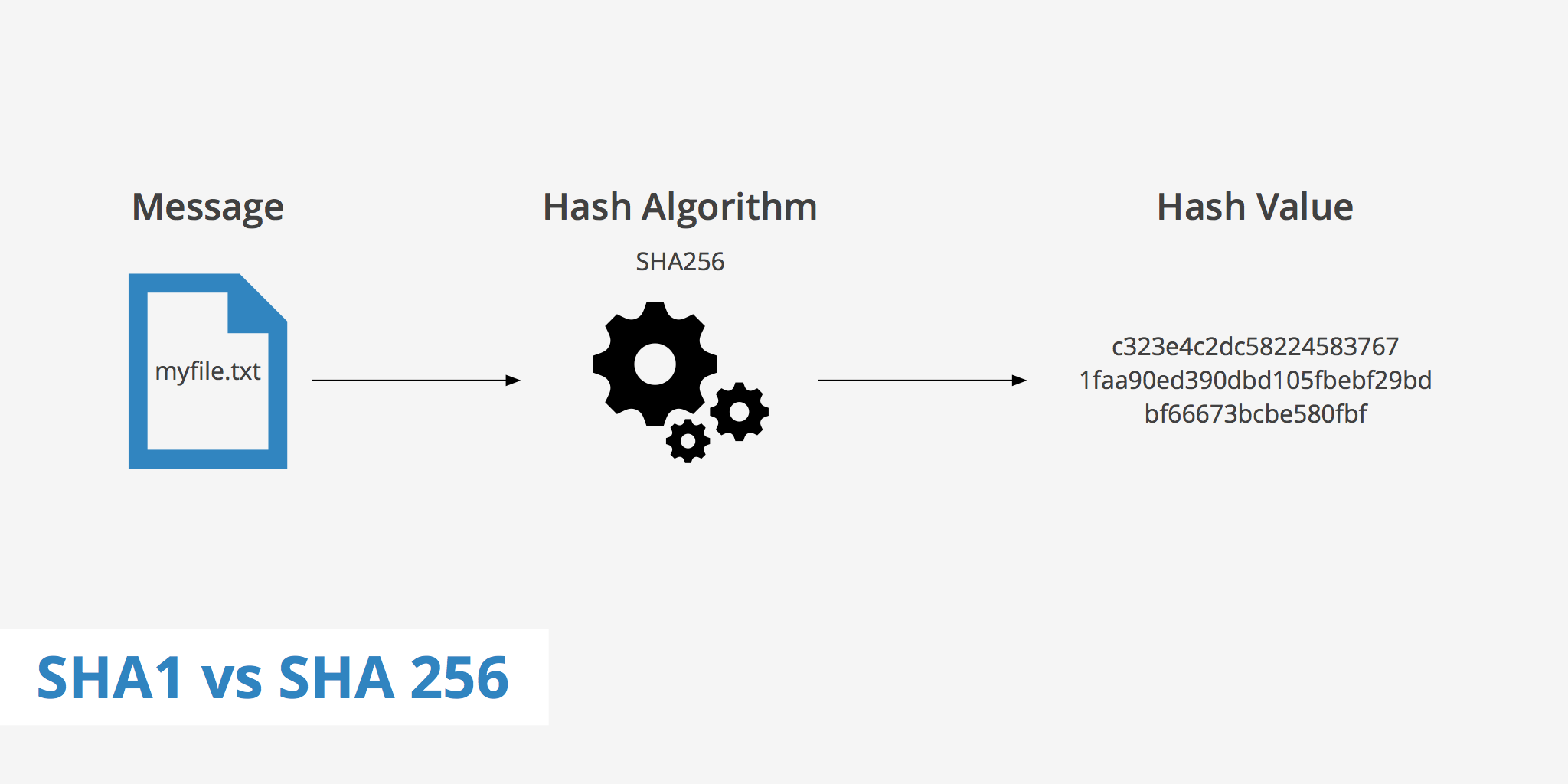
In the ever-evolving world of cybersecurity, strong hashing algorithms are essential for keeping data secure. One such algorithm that offers both efficiency and reliability is SHA-512/224, a member of the SHA-2 family. It’s designed to deliver the robust security of SHA-512 while producing a shorter 224-bit hash output, ideal for systems that require speed and compact data representation.
The SHA-512/224 Generator from ProfileLinks.xyz allows users to instantly convert any text or data into a secure 224-bit hash using the SHA-512/224 algorithm — ensuring your data remains tamper-proof and uniquely identifiable.
What Is SHA-512/224?
SHA-512/224 is a variant of the SHA-2 hashing algorithm, developed by the National Security Agency (NSA). It uses the same internal structure and mathematical strength as SHA-512, but trims the final output to 224 bits (28 bytes).
This design gives it the security benefits of 512-bit processing with the compactness of shorter hashes, making it an efficient solution for modern applications that demand both speed and integrity.
In simple terms:
- It’s based on SHA-512 computations.
- It produces a 224-bit hash output.
- It’s suitable for systems that need shorter hash lengths without sacrificing strength.
How Does SHA-512/224 Work?
SHA-512/224 follows the same process as SHA-512 but modifies the initialization vectors and output truncation. The main steps include:
- Preprocessing and Padding: The input data is converted to binary and padded to ensure it fits into 1024-bit blocks.
- Block Processing: Each 1024-bit block is divided into smaller 64-bit words and processed through 80 rounds of transformations.
- Message Expansion: Logical operations (like XOR, bit shifts, and rotations) expand the data to enhance entropy.
- Compression Function: Using constants and predefined functions, each round transforms the data into intermediate hash values.
- Truncation: Finally, the resulting 512-bit hash is truncated to 224 bits to form the final SHA-512/224 digest.
This design ensures SHA-512-level internal strength while maintaining efficient output size.
Why Use SHA-512/224?
The SHA-512/224 algorithm provides an ideal balance between security, efficiency, and output size, making it highly versatile. Here’s why many developers and organizations choose it:
- 🔒 Strong Security: Built on SHA-512’s architecture, resistant to collision and preimage attacks.
- ⚙️ Efficient Hash Size: Produces a shorter 224-bit output, ideal for applications requiring compactness.
- 🚀 Optimized for 64-bit Systems: Performs exceptionally well on modern processors.
- 💾 Reduced Storage Requirements: Shorter hashes save space without compromising integrity.
- 🧠 Standardized by NIST: Approved for government and enterprise-grade security systems.
Where Is SHA-512/224 Used?
SHA-512/224 is used in various fields where cryptographic hashing is essential for integrity, verification, and authentication:
1. Data Integrity Checks
Developers use SHA-512/224 to generate checksums for files, ensuring they remain unaltered during transfers or storage.
2. Digital Signatures
It’s used in digital signing systems where shorter hash outputs improve efficiency without reducing security.
3. Password Hashing
While specialized algorithms (like bcrypt) are recommended for password storage, SHA-512/224 can be used in combination with salts for extra protection.
4. Cryptographic Protocols
SHA-512/224 is integrated into encryption frameworks like TLS and PGP for secure communication.
5. Blockchain and Smart Contracts
In certain blockchain systems, SHA-512/224 helps with lightweight hashing and verification processes.
How to Use SHA-512/224 Generator
Using the ProfileLinks.xyz SHA-512/224 Generator is fast, private, and straightforward:
- Enter your text or data in the input field.
- Click “Generate Hash.”
- Instantly get a unique 224-bit SHA-512/224 hash output.
- Copy or save the hash for later verification or use in your project.
The tool processes all data locally in your browser — ensuring privacy and zero data storage.
Advantages of SHA-512/224
SHA-512/224 delivers several key benefits for both developers and organizations:
- ✅ Compact yet powerful: Shorter hash output without reduced strength.
- ✅ Cross-platform: Works efficiently across modern 64-bit systems.
- ✅ Resistant to attacks: Virtually impossible to reverse-engineer.
- ✅ Standardized security: Recognized under FIPS 180-4 guidelines.
- ✅ Versatile: Ideal for databases, APIs, and secure communications.
Its shorter output size (224 bits) makes it particularly useful where space or bandwidth is limited — such as embedded devices, IoT, or lightweight cryptographic systems.
SHA-512/224 vs Other Algorithms
AlgorithmBit OutputSecurity LevelPerformanceUse CaseSHA-1160 bitsWeakFastLegacy systemsSHA-256256 bitsStrongEfficientGeneral hashingSHA-512512 bitsVery strongModerateHigh-security systemsSHA-512/256256 bitsVery strongHighBalanced systemsSHA-512/224224 bitsStrongVery fastCompact security applications
SHA-512/224 offers excellent speed and secure hashing with minimal resource consumption, making it ideal for large-scale or mobile applications.
Why SHA-512/224 Matters in Modern Cryptography
The rise of data breaches, identity theft, and digital fraud has made cryptographic algorithms more critical than ever. SHA-512/224 provides:
- A trustworthy standard for modern security frameworks.
- Efficient compatibility with both legacy and cutting-edge systems.
- Reduced storage overhead with uncompromised safety.
It’s a practical solution for developers seeking strong cryptographic protection while keeping system resources optimized.
Why Use ProfileLinks.xyz SHA-512/224 Generator
ProfileLinks.xyz offers a free and reliable online SHA-512/224 Generator that prioritizes privacy and performance.
With this tool, you can:
- Generate secure 224-bit hashes instantly.
- Validate data integrity in seconds.
- Experiment with SHA-2 algorithms for learning and research.
- Strengthen your application’s cryptographic layer.
No installations, no logins, and no tracking — just fast, secure hashing right in your browser.
Conclusion
The SHA-512/224 Generator is a powerful tool for anyone who needs fast, secure, and compact data hashing. It combines the unmatched reliability of SHA-512 with the practicality of a 224-bit output, making it a perfect fit for developers, cybersecurity professionals, and IT administrators.
Whether you’re validating files, generating digital signatures, or ensuring message authenticity, SHA-512/224 offers an optimal balance between speed and security.
Use the ProfileLinks.xyz SHA-512/224 Generator today to safeguard your data with next-level encryption precision.
Popular posts
-
Random number generatorGenerator tools • 171 views
-
Emojis removerText tools • 168 views
-
Lorem Ipsum generatorGenerator tools • 165 views
-
Reverse lettersText tools • 159 views
-
Old English text generatorText tools • 158 views