SHA-3/384 Generator
Created on 30 September, 2025 • Generator tools • 120 views • 3 minutes read
Learn about SHA-3/384 generator: secure hashing, benefits, real-world applications, and how to generate SHA-3/384 digests.
SHA-3/384 Generator — Advanced 384-Bit Cryptographic Security
Introduction
In today’s digital age, secure hashing algorithms are essential for protecting sensitive data, verifying file integrity, and ensuring digital trust. Among modern algorithms, SHA-3/384 offers robust security with a 384-bit hash output, making it ideal for applications requiring strong, future-proof cryptography.
The SHA-3/384 Generator on ProfileLinks.xyz allows users to instantly create SHA-3/384 hashes from text, passwords, or file content — providing secure, tamper-proof, and unique outputs for digital integrity and authentication purposes.
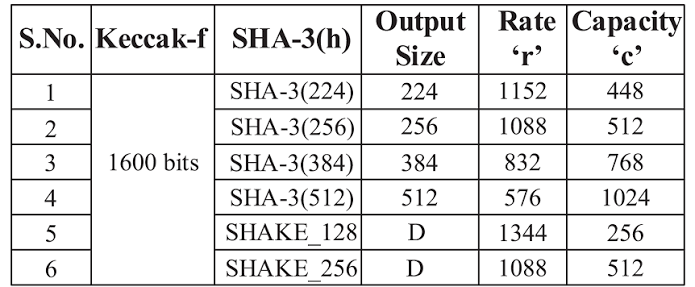
What Is SHA-3/384?
SHA-3/384 is a member of the SHA-3 family, the latest series of Secure Hash Algorithms standardized by NIST in 2015. Unlike SHA-2, SHA-3 is based on the Keccak sponge function, offering a completely different internal structure for cryptographic strength.
Key features:
- 384-bit output (48 bytes)
- Uses sponge construction instead of Merkle–Damgård structure
- Resistant to collision, preimage, and length-extension attacks
- Provides cryptographic diversity compared to SHA-2
SHA-3/384 is particularly useful for securing critical data, digital signatures, and applications that require high security with slightly shorter output than SHA-512.
How SHA-3/384 Works
SHA-3/384 follows the sponge function principle, which absorbs input data and squeezes out the hash output:
- Absorbing Phase: The input data is first converted into binary and divided into fixed-size blocks. These blocks are absorbed into the internal state using XOR operations.
- Permutation Function: Each block undergoes multiple rounds of nonlinear permutations, mixing and diffusing the data thoroughly.
- Squeezing Phase: After absorption, the algorithm extracts the first 384 bits of the internal state as the final SHA-3/384 hash.
- Output: The result is a unique, irreversible 384-bit hash, suitable for secure storage, verification, or digital signatures.
The avalanche effect ensures that even a single-bit change in input produces a completely different hash output.
Why Use SHA-3/384?
SHA-3/384 offers several advantages for secure digital operations:
- 🔒 High Security: Based on a completely different cryptographic design than SHA-2.
- 🧠 384-Bit Hash: Strong enough for enterprise-grade security without the overhead of 512-bit output.
- ⚙️ Resistant to Known Attacks: SHA-3 resists collision and preimage attacks effectively.
- 💾 Ideal for Digital Signatures: Perfect for signing messages, files, and certificates.
- 🌐 Versatile: Used in blockchain, secure messaging, file verification, and authentication.
Applications of SHA-3/384
1. Data Integrity Checks
Use SHA-3/384 hashes to verify that files or messages have not been altered during storage or transfer.
2. Digital Signatures
Many cryptographic systems adopt SHA-3/384 to sign documents and verify authenticity, thanks to its strong collision resistance.
3. Password Security
When combined with salt and key-stretching, SHA-3/384 offers robust protection against brute-force attacks.
4. Blockchain Applications
SHA-3/384 is used in some blockchain systems for transaction validation and secure ledger verification.
5. Cryptographic Protocols
The algorithm is applied in modern cryptography standards for authentication, message integrity, and token generation.
How to Use SHA-3/384 Generator
Using the SHA-3/384 Generator on ProfileLinks.xyz is fast and simple:
- Enter the text, password, or data in the input field.
- Click “Generate SHA-3/384 Hash.”
- Receive a 384-bit hash instantly.
- Copy or save the hash for verification, authentication, or secure storage.
The tool runs entirely in-browser, ensuring privacy and no data logging.
Advantages of SHA-3/384
- ✅ Strong 384-bit Encryption: Resistant to advanced attacks.
- ✅ Collision Resistant: Each input produces a unique hash.
- ✅ Efficient Output Size: 384 bits strikes a balance between security and storage efficiency.
- ✅ Versatile Usage: Suitable for files, passwords, blockchain, and digital signatures.
- ✅ Modern Cryptography: Uses SHA-3 sponge construction for enhanced security.
SHA-3/384 vs Other Algorithms
AlgorithmOutput SizeSecurity LevelPerformanceUse CaseSHA-1160-bitWeakFastLegacy systemsSHA-256256-bitStrongEfficientGeneral hashingSHA-384384-bitVery StrongModerateEnterprise securitySHA-512512-bitExtremely StrongSlowerMaximum securitySHA-3/384384-bitVery StrongModerateAdvanced cryptography, digital signatures
SHA-3/384 provides modern security comparable to SHA-2, with the benefit of a different underlying structure, enhancing cryptographic diversity.
Best Practices for SHA-3/384 Hashing
- 🔐 Use salting for password storage.
- 🧱 Combine with HMAC for message authentication.
- ⚙️ Always use secure channels (HTTPS) for transmitting hashes.
- 🔄 Keep updated with cryptography standards and NIST recommendations.
Educational Benefits
SHA-3/384 is not only a security tool but also a learning resource:
- Understand the sponge function principle.
- Observe the avalanche effect in cryptographic hashing.
- Compare SHA-3 outputs with SHA-2 for deeper cryptography insights.
- Learn practical applications in blockchain, SSL, and secure communications.
Why Use ProfileLinks.xyz SHA-3/384 Generator
ProfileLinks.xyz offers a fast, free, and secure online SHA-3/384 generator:
- Runs entirely in-browser with no installations.
- Generates instant and reliable hashes.
- Ensures privacy and zero data storage.
- Ideal for developers, security professionals, and students experimenting with cryptography.
Conclusion
The SHA-3/384 Generator is a powerful tool for anyone needing secure, 384-bit hashing. By combining SHA-3’s modern sponge construction with a 384-bit output, it provides robust protection, data integrity, and cryptographic reliability.
Whether you are verifying files, securing passwords, signing documents, or exploring blockchain applications, SHA-3/384 ensures your digital data remains tamper-proof and trustworthy.
Use the ProfileLinks.xyz SHA-3/384 Generator today to create secure, tamper-resistant hashes with next-generation cryptographic standards.
Popular posts
-
Random number generatorGenerator tools • 171 views
-
Emojis removerText tools • 168 views
-
Lorem Ipsum generatorGenerator tools • 165 views
-
Reverse lettersText tools • 159 views
-
Old English text generatorText tools • 158 views